Secure
Beacen vSeries provides proactive security, rather than reactive reporting and isolation. It’s system architecture eliminates attack vectors and attachment points that are exploited by malware and viruses. Beginning with network attachment each zStation contains an Open 64 port vSwitch that extends SDN rules to the edge. All network traffic can be separated and segregated, by application through this layer effectively extending data center grade network level protection all the way to the edge.
Application level containment and security is provided through three methods (i) Secure Sandbox (ii) Secure Dock and (iii) Secure Containers, each of these methods are described below.
- Secure Sandbox: Every application executing on a zStation endpoint are allocated their own memory heap, so there is no sharing of resources among applications. To put it more simply: Applications running in a sandbox are very restricted, and can't read or write to files that aren't explicitly allowed. Unless explicitly permitted.
- Secure Dock: Is a lightweight, stand-alone, executable package of a piece of software that includes everything needed to run it: code, runtime, system tools, system libraries, settings. Containerized software will always run the same, regardless of the environment. Containers isolate software from its surroundings, for example differences between development and staging environments and help reduce conflicts between teams running different software on the same infrastructure. Secure Dock containers isolate applications from one another and from the underlying infrastructure. Docker provides the strongest default isolation to limit app issues to a single container instead of the entire machine.
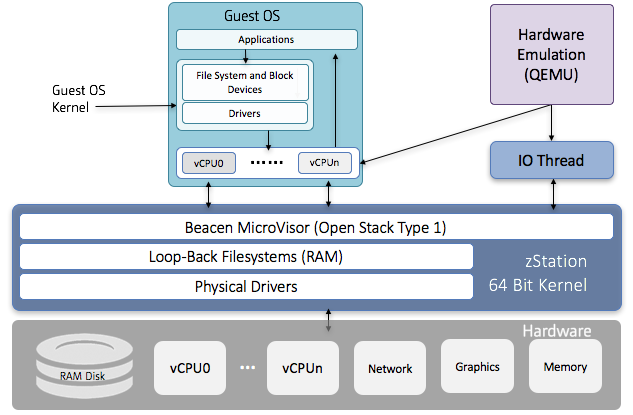
- Secure Container: Optionally zStation can be configured as a Type 1 hypervisor capable of supporting virtual machine guests that are completely isolated from the host zStation system. Theses virtual machines can be loaded over the network or alternatively stored in local secure cache which is AES loop encrypted at rest. Guests can operate either with direct access to the underlying hardware or through emulation mode.
Beacen vSeries Benefits
Plug-and-Play
Your computer becomes a true plug-and-play appliance, capable of working "out of the box" without the need for any administrative intervention. The installer only has to plug it in; and turn it on.
Fully Responsive
As technology continues its steady migration to mobile platforms it is not enough for the application to be the only responsive element. zStation’s modularity guarantees a completely responsive environment.
Secure
vSeries represents a new level of security, reducing if not eliminating attack vectors. Since the filesystem that the operating system resides on is read-only attachment points for viruses and malware simply don’t exist.
In-Memory
zStation endpoint operating environment operates exclusively in volatile RAM not requiring local storage for any operation. This architecture provides performance not attainable by traditional computer architectures.
Stateless
Remember when your computer was new, everything was fast and it just worked, as it gets older your computer seems slower, that’s because it is, operating system decay is a real issue. Since zStation is stateless it is new evry time you login.
Consistent
Policy based computing guarantees that the system is deployed in the ideal configuration. Both operating system and application workloads are always in the optimal configuration on all systems.